Modern attacks rarely come through “obvious” channels anymore.
● Ransomware, phishing kits, and command‑and‑control traffic largely use standard web ports and encrypted HTTPS, blending in with normal browsing and SaaS use.
● At the same time, employees now work from everywhere, on unmanaged or semi‑managed devices, hitting cloud apps the corporate network does not own.
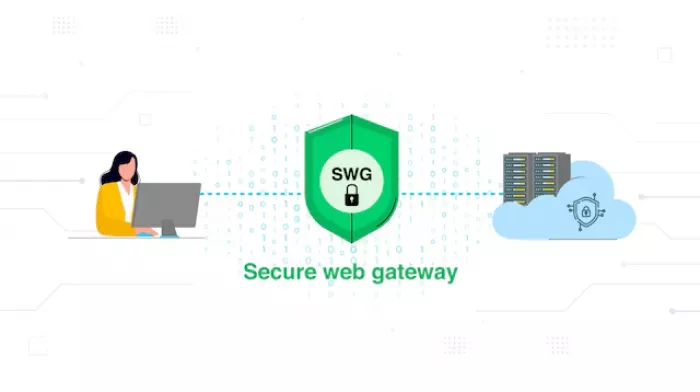
A secure web gateway (SWG) directly addresses this shift by inspecting all web traffic (inbound and outbound), decrypting it where needed, and applying granular security and compliance policies at the edge.

Gartner defines a secure web gateway as a solution that protects users on internet‑connected devices from web‑borne threats while enforcing corporate and regulatory policy compliance. At minimum, it provides URL filtering, malware and malicious code detection, application‑level controls for popular web apps, and data loss prevention (DLP).
Technically, SWGs act as a proxy between users and the internet, often decrypting SSL/TLS traffic to inspect content, apply security engines (AV, sandboxing, ML), and then re‑encrypt traffic before forwarding it. Modern offerings are increasingly cloud‑delivered and form a core building block of secure access service edge (SASE) architectures.
SWGs are critical because most attacks are now “web‑first”: drive‑by downloads, phishing pages, malicious ads, and weaponized SaaS links all rely on standard web traffic to bypass legacy perimeter tools. By inspecting both incoming and outgoing web sessions, SWGs can block malicious sites at the point of click and stop data exfiltration attempts leaving the network.
They also address the rapid growth of encrypted traffic: a majority of web traffic is now HTTPS, and attackers increasingly hide malware and C2 inside encrypted sessions that simple firewalls cannot see; HTTPS inspection within SWGs closes this blind spot.
● Advanced threat prevention: SWGs combine URL reputation, signature‑based detection, sandboxing, machine learning, and behavior analysis to block malware, ransomware payloads, and zero‑day phishing pages in real time.
● Deep visibility and HTTPS inspection: By decrypting and re‑encrypting SSL/TLS traffic as a proxy, SWGs gain full visibility into URLs, payloads, and file content, including threats hidden in encrypted sessions.
● Data loss prevention and compliance: SWGs can scan outgoing web and cloud traffic for sensitive data patterns (such as financial records or customer PII) and block or alert on unauthorized transmission.
● Application and user‑level control: Modern SWGs understand specific web apps and can control actions like upload, download, share, or sync based on user identity and role.
● Stopping ransomware at the web layer: Vendors report that SWGs can block ransomware campaigns early by detecting malicious file downloads and preventing users from reaching exploit kits and phishing pages used to deliver initial payloads.
For example, advanced gateways use sandboxing and ML to detonate suspicious downloads and block them before they hit endpoints, reducing reliance on endpoint AV alone.
● Preventing data breaches via cloud apps: Organizations use SWGs to enforce DLP rules on uploads to cloud storage or file‑sharing services, preventing accidental or malicious uploads of customer data.
● Improving phishing defense beyond email: Even when a phishing email slips through, SWGs can still block the final phishing URL or fake login page the user clicks, cutting off credential theft.
SWGs in Remote Work Environments
With cloud‑based SWGs, security can follow users wherever they connect, rather than forcing all traffic back through a central data center via VPN. This reduces latency while keeping the same policy set and inspection depth for branch offices, home workers, and mobile devices.
In SASE designs, SWG capabilities sit alongside zero trust network access (ZTNA) and CASB, giving remote workers secure access to both web and private apps through a unified, cloud‑native edge. This architecture is far better aligned with SaaS‑heavy, hybrid‑work realities than traditional hub‑and‑spoke networks.
● Encrypted traffic blind spots: Attackers hide malware and C2 traffic in HTTPS to evade legacy inspection; SWGs perform SSL/TLS decryption and deep inspection to uncover these threats.
● Shadow IT and SaaS sprawl: Employees often adopt unsanctioned web apps without security review; SWGs give security teams visibility into app usage and tools to control or sanction them.
● Regulatory and policy enforcement: Industries with strict compliance requirements must prevent sensitive data leakage over web channels; SWGs’ DLP, logging, and policy controls fill that gap.
They also help demonstrate due diligence by recording web access and policy decisions for audits and incident investigations.
SWGs are converging into broader SASE and security service edge (SSE) platforms, where web security, ZTNA, CASB, and firewall‑as‑a‑service share a unified cloud architecture and policy engine. This integration makes it easier to apply consistent, identity‑centric policies across web, private apps, and SaaS from a single control plane.
Artificial intelligence and machine learning are also becoming standard within SWGs, improving their ability to detect previously unseen phishing and malware campaigns from behavioral patterns rather than static signatures. Expect deeper integration with identity providers, device posture signals, and API‑level controls for SaaS, pushing SWGs further into the heart of zero trust strategies.
Modern cyber attacks ride on the same web protocols, ports, and encryption that legitimate business traffic uses, which means only controls sitting in the web path with deep visibility can reliably stop them. Secure web gateways provide that control point, combining advanced threat prevention, HTTPS inspection, DLP, and app‑aware policies in a form that scales to cloud and remote‑work realities.
For any organization serious about cyber defense, an SWG (ideally as part of a SASE or SSE stack) is no longer optional; it is a foundational layer that protects users, data, and applications from the dominant attack vectors of today’s internet.
Discussion